Every software-product developer should be familiar with the milestone-book "Don’t make me think" from Steve Krug, and probably lots of us read it.
I did, and I agreed!
This happened some years ago…
Nowadays my days runs faster, and it may happen that old precious hints get lost.
Some days ago, I called Massimo, an expert .NET developer, for testing our new product BugsVoice, but secretly to push it to develop, for free, an example of .NET page for catching errors (please don’t tell him).
He sat down in front of me (see our space here ) and started to enroll in BugsVoice.
I was peeping him over the monitors barrier watching his face struggling, and then I
remembered Steve’ rule, that actually is the all-month tips…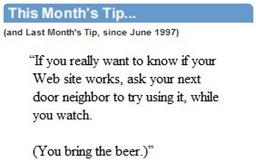
So I moved around the table and I sat behind him, really close, looking over the shoulder , to see both monitor and keyboard, like a crow on the shoulder…
I discovered in a half hour session that some parts of our application are hard to understand or completely unclear.
We have already used, with satisfaction, professional testing service like UserTesting for our products; they usually provide you a video file recording user voice and screen interaction, but seeing a “human” (are programmers human?) face give you an emotional feedback that you will miss in video files.
Some hints to get the best from user testing:
- give the tester a small overview of your product. Do not explain your product in detail, give only the context. Prepare a short story board: I gave my tester the following tasks: enroll, choose an error template, configure your server, collect some errors.
- invite the tester not to be shy and talk while playing with your app. Explain that it is not a competition, and that you are testing the application not the tester 🙂
- resist to interfere. Do not help your tester and take notes when the tester stops. Eventually hearten him and ask what’s the matter.
- look at the mouse movements. If the pointer goes around the screen without a goal, probably there is something too small, in a bad place, or too far. Take notes!
- look at the tester’s face. When you see self-satisfaction (seems that he/she is understanding something) ask what he/she thinks that feature is. Take notes!
- let the tester play whith you app discovering features. Take note of the path the tester follows to reach the goal. Is he using different/unplanned ways? Probably there is something to be done on the interface!
- look at the clock. Usually a “real” user does not give you more than few minutes before giving up. It is valuable to reach at least a rewarding step in the first minutes.
- at the session end ask the tester an overall impression of your application. Ask what he feels about each phase (enroll, step 1 etc.) and take notes
- then ask the tester some suggestions to refine your app. Take notes, but then throw them away, you already have a lots of better feedback.
In our case a thirty minute session gave me five A4 pages full of interesting notes.
What I wonder about user testing is that very often what misleads the user is a wrong message, a color in a title, a misplaced button, a hidden something; all things that you can fix in minutes and usually every programmer tends to underestimate. Of course sometimes you may get in serious trouble when you miss a core point; this is why it is crucial to start user testing very early. I know that it is sometimes hard to do, how to test an application if a core functionality is missing?
We started user testing quite late with BugsVoice alpha (internally), and we are continuing with the public beta.
Give yourself the opportunity of a day as a crow on the shoulder, you won’t regret it.


